Android Lollipop Screen Pinning
Android Lollipop allows third party applications to pin themselves to the device screen. Once the third party application activates screen pinning, users cannot see notifications, access other apps, or even return to the home screen, until the application exits the mode.
According to the Androdid Documentation, to activate screen pinning programmatically, call startLockTask().
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_main);
startLockTask();
String url = "http://www.example.com";
Intent i = new Intent(Intent.ACTION_VIEW);
i.setData(Uri.parse(url));
startActivity(i);
}
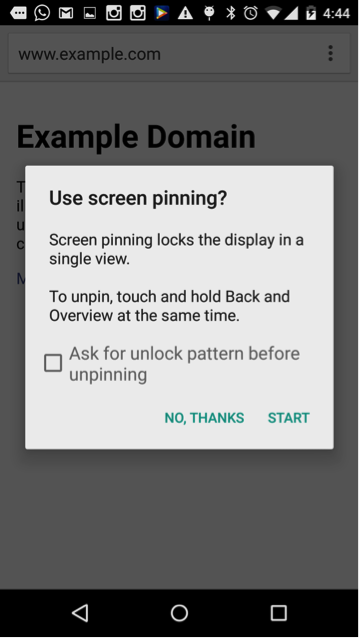
Since Screen Pinning can be performed programmatically, an app can trick the user into performing pinning. An application can initiate screen pinning and immediately launch another trusted application. In Fig 1, app A initiated screen pinning and launched the default browser, which can be seen on the background. Also, since pinning does not require any pre-defined permissions, the user does not know in advance if an application will programmatically perform pinning. Additionally, the visual indicators and consent message for pinning being performed manually and programmatically and the same and the message does not display the name of that application that initiated screen pinning.
 </img>
</img>The user looking at the screen may think the screen pinning has been initiated by the trusted default browser in the background and would press START to enable screen pinning. This would pin the app A to the user’s screen. App A can now launch phishing attack since the user thinks the default browser is enabled, not app A. Since App A is the pinned state, the user sees no notification, cannot see the recent list of application or go to the home screen without stopping pinning, which gives the app a higher rate of success to phish the user. To exit pinning the user has to press the recents + back button’s together.